Insurance Industry
The Government Beckons

Like Apple, insurance carriers and brokers hold an enormous amount of sensitive client information.
Unlike Apple, they are unlikely to find themselves in a highly public battle with the FBI should they resist demands for that data, as the tech giant did last spring in a dispute with the agency over the information in a terrorist’s locked iPhone.
But in the future, companies in the insurance space should be on the lookout for requests from regulators in other circumstances. Not necessarily in the wake of a mass shooting, but in the aftermath of any number of cyber hacks, the course of investigating a car crash or as part of the effort to secure crucial energy infrastructure.
And according to at least one expert, they should consider dumping the use of smartphones for conducting any kind of company business.
Investigators may request insurance company client data collected or transmitted through smartphones, said Theodore P. Augustinos a partner with Locke Lord LLP. Although for now, he said, the dilemma is more theoretical than actual.
“The government could subpoena geolocation data collected through a fitness app,” he said, and that data could come into play if the insurance company received it.

Theodore P. Augustinos, partner, Locke Lord LLP
Investigators could also be interested in insurer-collected behavioral data, such as drinking and driving habits recorded by one or more apps that measure telematics and geolocation, said Hart Brown, vice president, organizational resilience, HUB International.
“That real-time data could be very powerful in a crime or accident investigation,” Brown said.
The crucial difference between the insurance community and Apple is that “Apple’s technology prevented access to the data,” Augustinos said.
In contrast, the insurance industry erects no technology barriers to the data it collects for its own use.
After 2015’s spate of cyber attacks that compromised 100 million records in health care — now the top industry for cyber attacks, according to recent IBM research — insurers should be “concerned” about federal investigators possibly seeking information, said Adam Cottini, a managing director in the cyber-liability practice with Arthur J. Gallagher & Co.
He predicts more and varied attacks, and more investigations, in industries involved in national security and critical infrastructure.
“We’ll see a level of investigative activity that rivals what we saw with the iPhone. Marine, utilities, water companies, the power grid — insurers house information from these industries, and the information they provide may rise to the level of national security and critical infrastructure.”
“An attacker who has your business card knows who you are, your employer, your position and the address to the device in your pocket during meetings and conversations.” — Michael Nash, president, Privacy Research, Inc.
For now, those records don’t usually involve locked technology such as smartphones. As they have historically, investigators such as the FBI may request or subpoena that data as they see fit, Augustinos said, and “companies will continue to release client data as they see fit.”
Investigators fish for data wherever they can, and insurers may be the source of last resort for that kind of information.
“If they meet resistance from the telecom providers and device manufacturers, they may go to the carrier next,” Brown said.
Whether investigators request information from insurers, and whether insurers release it, will play out on a case-by-case basis, Brown said.
“Information has value, and protecting it creates brand value. Insurers want to be good citizens and will cooperate with an investigation of an identified threat, but we won’t see companies sharing information in a blanket manner.”
Hackers Know: To Err Is Human
Human behavior that leaves data and networks vulnerable to hackers is a bigger and more immediate problem than government intrusion, said Michael Nash, president, Privacy Research, Inc.
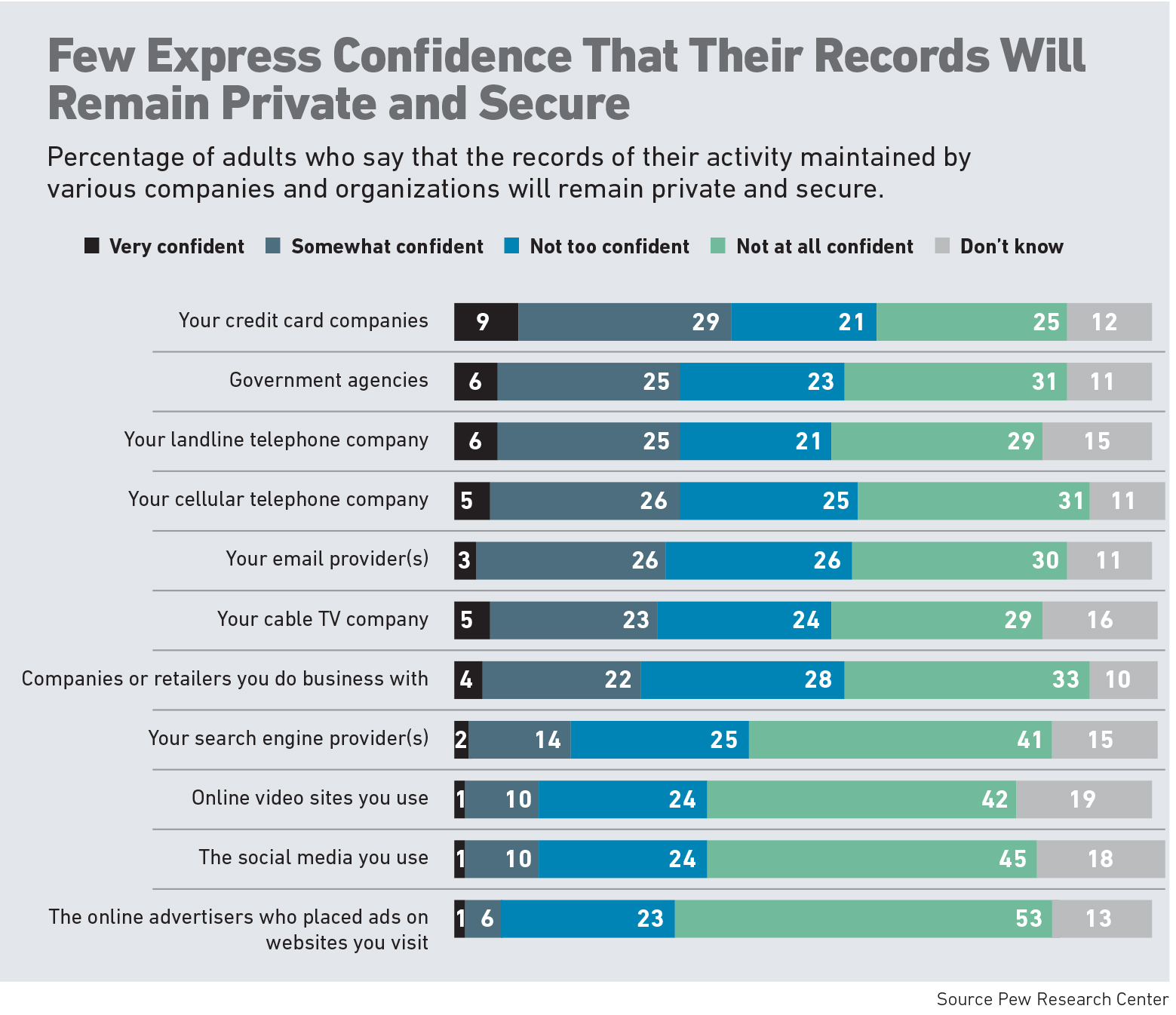
He is unequivocal about the dangers the widespread use of smartphones pose for all companies, not just insurance carriers.
“Smartphones are not appropriate for business use. People don’t understand that their trusted personal devices are computers — computers unprotected by effective antivirus software and firewalls, which makes them inherently untrustworthy.”
Smartphones can be compromised over the cellular network, he said, and also through Wi-Fi, Bluetooth, and NFC (Near Field Communication, the technology that allows transferring photos between phones by tapping their backs together).
“Your phone can be compromised anywhere — your home, the train, a coffee shop.” Some countries, especially China and Turkey, are notorious for attacks on travelers’ phones, he said.
Even locked networks, such as those in hotels, can be “spoofed” by opportunistic hackers waiting to prey on gullible users. Once the device is brought back to the office and joins the company’s network, the devices can be used as an entry point for network penetration.
“All an attacker needs is a cell phone number,” Nash said in an interview conducted on his own cell phone, which rang through a landline number, sparing him the necessity of divulging his cell phone number.
He recommends omitting cell phone numbers from business cards.
“Your cell phone number is an address for the device. An attacker who has your business card knows who you are, your employer, your position and the address to the device in your pocket during meetings and conversations.”
Not only can hackers access data on the phone, they can turn on the camera and microphone remotely without the owner’s knowledge — a great espionage tool in corporate meetings and secured areas. And turning the phone off provides no protection, Nash said.
Cottini sees risks when employees use the same device for business and personal use.
“Employees can slip up and send business emails from their Gmail accounts,” he said.
“Then the confidential business information is stored on the device, which isn’t secure, and the provider’s cloud system, which may have fallible security.”

Adam Cottini, managing director, cyber-liability practice, Arthur J. Gallagher & Co.
Whether or not the information has value to an intruder, Cottini said, the corporation’s intellectual property is vulnerable. Despite the high financial or reputational cost to corporations of smartphone-related losses, he doesn’t see corporations abandoning smartphones or returning to the outdated two-device model, one for personal use and one for business.
The solution, he said, and an imperfect one because it depends on human behavior, resides in training and technology.
“Ideally, you want a culture of security and awareness built into training programs that would check an employee’s habits of using a Gmail account,” Cottini said.
Employees can also use encryption apps, “but they’re useless — not if, but when — people use traditional cloud email to transmit corporate messages.”
Although it isn’t yet commonplace, Cottini said, virtualization technology exists now to separate employees’ personal assets on their phones from corporate assets, which when used correctly prevents corporate assets from residing on the phone.
Companies would have to approach those solutions delicately so employees don’t feel bullied, Cottini said.
“Employees will ask, ‘Why am I being told what to do with my own device?’”
No Fix in Encryption Alone
Long before the Israeli company Cellebrite Mobile Synchronization broke into the San Bernadino terrorist’s encrypted iPhone, a YouTube search for “how to break into iPhone” produced more than 6 million results, confirming what hackers and risk managers already knew: any encryption can be broken, inviting speculation that the iPhone-breaking incident may have been political theater to create a legal precedent for investigations involving locked technology.
“If you can make the technology, someone with enough resolve can break into it,” said Cottini.
Breaches of encrypted data are so routine that states are toughening their data breach laws; in July, Tennessee will become the first state to remove its encryption safe harbor.
This game of whack-a-mole calls for vigilance.
“You need multiple rings of security,” Cottini said, not just encryption.
“If hackers get to the other side of your firewall, you need to change all the failed protections that let them in. You need access controls, so only highly vetted people have access to sensitive data.
“Companies run the risk of complacency around their data,” said Kristen Gaebel, director, financial services regulatory practice, PricewaterhouseCoopers. Take a long, hard look at privacy and data protections, she advised.
“Perps are getting more sophisticated, and companies need to constantly evolve training, governance and risk assessment to identify susceptibilities.”
“Catch the bad guys by surprise,” Cottini said. “Rotate your defenses to be random. If they’re static, the bad guys will catch you.” &