Why Every Company Needs a Cyber Attack Response Plan No Matter Their Size — and Helpful Tips to Get Started

With ransomware attacks exponentially on the rise, all organizations need to prepare for cyber events.
Response planning, however, will vary greatly depending on the size of the organization.
And smaller businesses may have more work to do than larger ones: A recent Wall Street Journal survey found that 81% of companies with more than 1 billion in revenue have a cyber security program in place — just under two thirds of companies with less than $50 million in revenue could say the same.
“No matter the size of an organization, the drivers for planning how to respond to a cyber incident are generally the same: Being prepared to restore the integrity of data processing systems and restore business operations as quickly and responsibly as possible,” said Mari DeGrazia, associate managing director at Kroll and cyber risk and certified instructor at SANS Institute.
Even if the fundamentals are the same, when it comes to creating cyber response plans, different businesses have different needs.
Larger companies should be focused on larger threats while medium-sized businesses might want to focus on finding a balance on what security measures can be done in-house vs. what needs to be outsourced. Smaller companies should remember that in our current landscape, anyone can become the target of a cyber attack — and prepare accordingly.
Large Companies: Big Budgets, Big Threats
Experts sya that larger companies should expect attacks from more sophisticated actors.
“Cyber risks certainly change due to the size of the organization,” said Dave Wong, vice president of FireEye Mandiant.
“Larger companies are targeted by more sophisticated threat actors. The larger companies are targeted by ransomware actors, because of their deeper pockets. It’s not unusual for us to see extortion amounts greater than $10 million. Larger service providers and professional firms have more valuable data to steal.”

Dave Wong, vice president, FireEye Mandiant
Given the risks involved, larger, public or enterprise-size organizations are typically better prepared for cyber incidents, Wong said.
Larger companies have stronger governance about business continuity and risk in general, dedicated programs for risk mitigation and cyber harm reduction, and more budget dollars allocated to cyber security.
“The risk/reward calculation is likely going to be different based on size. For instance, if we assume that companies spend roughly the same as a percentage of revenue, larger companies will have a larger budget. Not everyone can spend $1B on cyber security like Bank of America,” he said.
Not only do larger organizations tend to have well-staffed in-house risk management and cyber security departments, but they also usually have cyber incident response firms, forensics providers, law firms and other contractors on retainer ready to help when an event occurs.
As some of the earliest adopters of cyber risk policies, enterprise level organizations are the most likely to have formal cyber incident response plans with multiple scenarios and to have tested them with tabletop exercises.
“Larger companies will have more detailed plans that address more situations and more detailed internal and external communication plans,” Wong said.
“There are more constituents to coordinate with, such as the board of directors, legal, compliance, communications, regulators, customers, etc. Larger companies will likely have matrices that describe how decisions are made. For example, who will decide on whether a ransom is paid or if a networks or systems should be shut down. Due to complexity of larger companies, there will be more planning to coordinate between internal teams.”
Given the bureaucracy in large companies, it can be vital to pre-negotiate contracts for vendors and plan incident communication trees to ensure that ordinarily complex internal processes are streamlined in an emergency situation, such as a ransomware event where every second counts.
Medium Size: Finding the In-House/Outsourcing Balance
Small- and medium-size businesses across all sectors that may have been less concerned about cyber security in the past are now more vulnerable to supply chain attacks.
These traditionally less protected networks and systems are used as a way to gain “weaker link” access to larger companies.
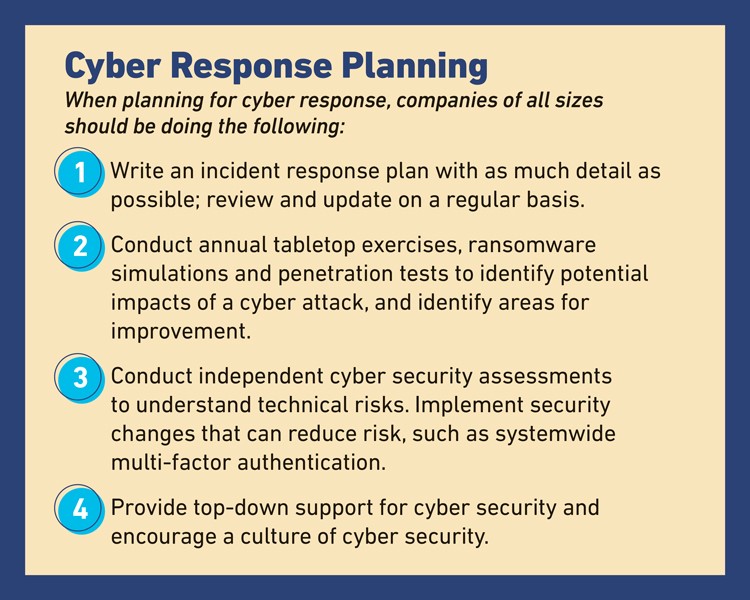
Medium size companies can run the gamut in terms of cyber event readiness, though generally speaking, companies in regulated industries such as finance and health care will tend to have more mature cyber security programs, Wong said.
Those are the most likely to have performed incident readiness assessments, retain contracts for incident response providers, and hold a solid cyber insurance policy.
Depending on the company’s culture and the value placed on cyber security, there may or may not be an in-house cyber security program. Increasingly, many medium-size companies are outsourcing cyber security whether through cloud-based security products, consulting or actual cyber security oversight to bolster defense.
“There is a growing business in virtual CISOs or part-time CISOs, especially with regulation requiring cyber security programs. I see this as a positive development, as smaller companies now have access to experts with years of experience. Hiring full time CISOs is difficult now, given the strong job market in cyber security,” Wong said.
“However, there is only so much one person can do. Companies that invest in cyber security by increasing their cyber teams and using consultants, managed security service providers can improve their posture.”
Other medium-sized companies have opted for a hybrid approach that optimizes budget dollars for maximum impact, said Lucie Hayward, senior vice president at Kroll.
“Medium organizations fall somewhere in between — they may choose to outsource certain functions such as monitoring but can also have dedicated cyber security resources.”
Small Companies: Not as Invisible as They Used to Be
Perhaps unsurprisingly, small companies are typically the least prepared for cyber attacks.
One reason is that historically they were not targeted as frequently. As a result, most still don’t have a retainer for an incident response firm or an incident response plan in place. However, the myth that small companies can fly under the radar from cyber threat actors simply no longer holds true.
“Even if a threat actor isn’t necessarily targeting small companies, there’s a lot of hacking going on out there,” said Mark Greisiger, president of NetDiligence. “If you’re a smaller company, your system is responding to the hacker’s software — and they’ve found your weakness. And that’s why they go in and exploit it.”

Mari DeGrazia, associate managing director, Kroll
What’s more, the stakes are often much higher for small companies.
When a ransomware or DDoS attack hits an unprepared target, business interruption costs, response services and legal fees — not to mention hefty ransom payments may be a veritable death knell.
“A cyber attack on a small firm can be an ‘existential event,’ ” Wong said. “B2B companies that have other businesses as customers will see companies freeze business or walk away during a cyber incident.”
Given that smaller businesses tend to use less documentation and protocols, it’s crucial that cyber incident response planning includes an actual, written plan.
“When you’re talking about ransomware and cyber attacks, you need a very granular, specific plan with action steps and external experts to help you recover,” Greisiger said.
“Large or small, it’s increasingly important to companies that the experts are trusted and privileges are protected.”
While a large organization might bring in a law firm to assist with incident response plan development, a small- or medium-size firm that can’t afford a $30,000 line item can opt to use an online service that will walk them through the process yet still allow for a customized plan.
For a smaller company, the plan itself may be less involved, given fewer locations, operations, staff, systems, customers and networks involved. There’s also less of a need for a decision matrix — it will likely be a single person, such as the CEO, who makes the call as to whether to pay a ransom or whether the network is shut down.
In a smaller business, however, employees might be more apt to wear different hats, so it is crucial employees are properly trained on incident response procedures and security protocols.
“For small organizations, it’s not always feasible to have dedicated cyber security resources on staff, so many will outsource some or all their IT operations, including security,” DeGrazia said. “For these organizations, a large part of incident response planning will rely on the managed service provider (MSP) to handle the technical components of an event.”
While engaging an MSP may be a cost-effective choice for a small organization, DeGrazia said there is always a risk the MSP might not have appropriate controls or may not escalate a suspected incident when they should and could potentially delay the response. For that reason, small companies should take extra care when engaging with an MSP.
“Any organization that chooses to outsource IT operations should request to review their MSP’s incident response plan,” Hayward said.
”Additionally, the organization should require a defined service level agreement for reporting suspected cyber security incidents and providing information to the organization in a timely manner. The MSP should also be required to maintain a specified level of controls, as well as retaining detail logs for a specified amount of time.” &










