Retail Data Exposures
Emerging Ways to Pay
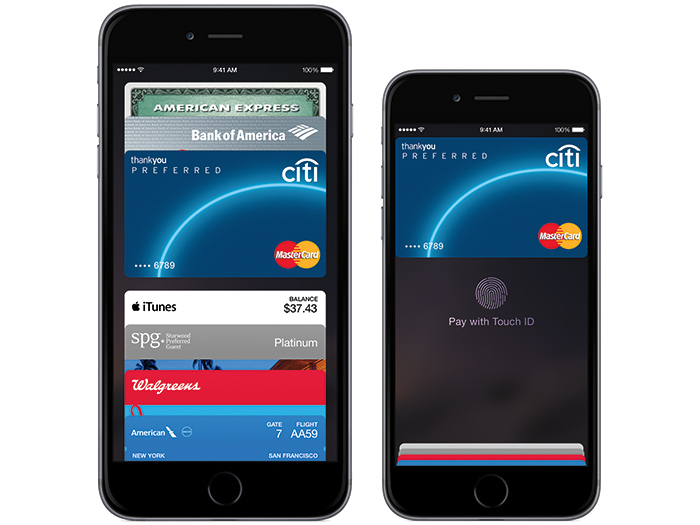
With massive data breaches among big box retailers and major banks consistently making headlines, the cry for more secure consumer payment methods has reached a crescendo.
Yet, the critical question remains: Will emerging technologies — from “chip/pin” credit cards to Apple Pay, Google Wallet and other similar e-payment products — stem the data risk tide?
And if so, will there be a winner among the group? Will there be a single payment system that can give both retailers and their customers a sense of security that currently doesn’t exist?
It’s much too early to tell, experts said. The main challenge now may be sorting through the various technological options — in addition to the potential cost and difficulty of implementing a new standard system.
Video: Mashable took Apple’s new payment system to the streets of New York City to see how it worked.
For example, some large retailers such as Wal-Mart, Rite Aid and CVS recently announced they would not accept Apple Pay, which uses the iPhone and major credit cards as its “touchless” payment delivery system.
Those large retailers and others are planning to use an alternative e-payment technology, called CurrentC, which bypasses major credit cards completely. The retailers favor that system because it eliminates the transaction fees charged by credit card companies to retailers.
According to Aaron Press, director of e-commerce and risk solutions at LexisNexis Risk Solutions in Dallas, each of the various mobile wallet systems has its own advantages.
One key benefit of systems such as Apple Pay and CurrentC is that they do not pass actual card data to the merchant, so there is no account information either in storage or in transit that can be compromised.
“If the wallet systems are secure, then consumers benefit from not sharing their payment credentials with merchants,” he said. “This means that even in the event of a breach, the consumer will not have to worry about their information being stolen and dealing with the hassle of disputing fraudulent charges or receiving new account numbers.”
In addition, said David Katz, leader of the privacy and information security practice group at Nelson Mullins in Atlanta, Apple Pay’s biometric Touch ID technology makes it “difficult for a thief or imposter to use an iPhone to complete transactions fraudulently.
“Consumers whose phones are stolen or misplaced can easily use the ‘Find my iPhone’ feature to suspend all payments,” he said.
“Even if the world magically adopted chip/pin technology overnight, hackers would simply find a new way to turn card data into money.” — Russ Spitler, vice president of product management, AlienVault
However, he added, with 800 million credit cards on file — not to mention the brand new watch/fitness trackers that contain large amounts of health data — Apple may have succeeded in making itself the primary target.
Press noted that it is not yet clear whether Apple Pay or CurrentC will be vulnerable to fraudulent use.
E-wallet providers must ensure that the credentials being provisioned and used actually belong to the consumer attempting to use them, and that the applications, processes and infrastructure are secure, he said. The biometrics used with the Apple Pay process are helpful, but not a panacea.
Biometric Advances
Apple Pay, however, represents a security improvement over magnetic stripe architecture since it requires stealing a victim’s phone and successfully duplicating their fingerprint to commit fraudulent transactions, said Paco Hope, principal consultant at security consulting firm Cigital, in Dulles, Va.
Apple Pay also includes architecture (such as proxy numbers instead of account numbers) that contributes additional security, he said.
Russ Spitler, vice president of product management at AlienVault, a security provider in San Mateo, Calif., called Apple Pay a “major move” for the payment industry.
While the underlying technology is not new, Apple has the market share and mindshare to make it popular, he said. Shifts in payment technology are driven by consumer demand, not retailer preference.
“In the past, Apple has proven to manage private data very responsibly — they take encryption seriously and implement it well,” Spitler said. “They are still prone to attacks against their users such as the recent iCloud issues — but they are working to add more features to help safeguard even in that situation.
“With Apple Pay, I am hopeful we will turn the corner on the horrible status quo of credit cards,” he said.
Structural Challenges
Because the U.S. adopted credit cards faster than they spread across Europe, Spitler said, the infrastructure in the U.S. is antiquated and entrenched, such as the point-of-sale (POS) systems reliant on magnetic stripe technology.
Moving past that to new EMV-based credit cards (also referred to as chip-and-PIN, chip-and-signature, chip-and-choice, or generally as chip technology) will require a major retrofit of a very distributed payment system in use for a long period of time, he said.
Video: A brief look at some of the advantages and challenges with EMV technology.
“Each corner store will have to invest in new technology at great cost to themselves and without any demand from the consumer; that’s a really difficult request to make of a small business,” he said.
EMV supports dynamic authentication (numbers change with each transaction), which means a cardholder’s data is more secure on a chip-enabled payment card than on a magnetic stripe card, and is much more difficult to copy or counterfeit.
“Magnetic stripe technology makes it dirt simple to clone a card once you have the electronic data associated with it,” Spitler said.
However, he said, the use of chip/pin technology does not guarantee the long-term elimination of risk.
“Even if the world magically adopted chip/pin technology overnight, hackers would simply find a new way to turn card data into money,” Spitler said.
Hope said that payment networks are introducing risk management beyond simply accepting or denying charges. Contactless payment systems deployed in the UK, for example, are usually dependent upon a variety of limits on total amount, number of transactions and transactions per time period.
“This is what it looks like when modern risk management meets the retail experience: the strength of the security measures in place,” he said. “Retail customer data in the future will be much more carefully protected using similar designs.”
Cyber Coverage
Regardless of what type of payment system is used, Collin Hite, who leads the insurance recovery group at Hirschler Fleischer in Richmond, Va., said all businesses should have cyber insurance, even though many companies still don’t believe they are likely targets.
The first party aspects of such coverage can be critical to a business since the insurance pays for forensic investigation and re-securing the network, in the event of a data breach, he said.
“This is typically the largest cost — not the actual loss of information of the consumers,” he said.
“While we know the Fortune 500 to 1000 are considering specific cyber coverage, middle-market businesses need to understand that they are as vulnerable as the ‘big boys,’ ” he said.
Craig Young, a mobile security researcher for Tripwire, in Portland, Ore., said the best risk management strategy is to move to the next technology as quickly as possible.
“The ancient swipe and sign technology that dominates American retail is long overdue for a funeral,” he said. “For years, credit cards have been low-hanging fruit for thieves with a variety of techniques to steal card data, reproduce cards and start spending.”
LexisNexis’ Press added that it’s way too early to declare a front runner in mobile payments, and that magnetic stripe cards will be around for several more years.
“There is no security salvation or fraud magic bullet, but many of the new technologies offer a lot of promise,” Press said. “EMV will drastically improve POS security and reduce counterfeit fraud. Biometrics is a promising option for identity verification.”
But, he warned, new technologies can open the window to new problems while shutting the door to known issues. Adding new technologies such as mobile, he said, increases the number of potential blind spots.
“Companies need to evaluate the risks and benefits of adding any new commerce technology or channel to their environment,” Press said.










