Sponsored Content by QBE North America
Financial Services Sector Faces Heightened Cyber Threats

The financial services sector is under increasing cyber threat as ransomware attacks and data extortion tactics pose significant risks, according to a white paper by the QBE Cyber Threat Intelligence Team. Despite their heightened security investments, even major financial institutions are falling victim to sophisticated attacks that disrupt operations and compromise sensitive customer information.
Ransomware remains the top threat to all organizations, including those in financial services, in terms of likelihood and potential impact. The criminal ecosystem has evolved to enable threat actors to easily gain access to corporate networks through various methods like exploiting vulnerabilities, phishing and purchasing credentials on the dark web. Advanced threat actors are consistently adopting new and effective techniques to evade detection, steal data and deploy ransomware enterprise-wide.
Much of the ransomware landscape is dominated by the ransomware-as-a-service (RaaS) model. This is reflected in the interplay between initial access brokers who gain entry to networks, affiliates who carry out the attacks and RaaS operators who provide the ransomware infrastructure. In 2023, the financial services sector was the fourth most targeted, with 346 victim organizations listed.
Several notable ransomware incidents impacted the financial sector in 2023 and 2024:
- In February 2023, the ION attack by LockBit disrupted derivatives trading.
- The Latitude Financial extortion attack in March 2023 compromised the personal data of 7.9 million customers.
- From March to July 2023, the Clop ransomware group exploited the MOVEit vulnerability, impacting roughly 100 companies.
- In November 2023, a spate of attacks potentially linked to the Citrix Bleed vulnerability breached companies including ICBC, TCW, MeridianLink and FNF.
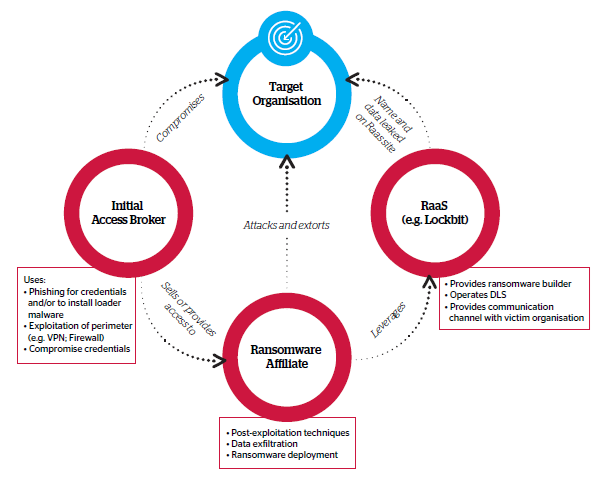
Evolving Tactics Enable Threat Actors to Infiltrate Networks
The direct exploitation of vulnerabilities in external-facing infrastructure remains a primary intrusion vector for threat actors targeting financial services organizations.
In 2023, zero-day vulnerabilities in widely used applications like MOVEit and Citrix NetScaler enabled widespread attacks before patches were available and implemented by organizations. The exploitation of these vulnerabilities led to spikes in the number of victims, catching many large organizations off guard. As the technical proficiency of organized crime groups grows and zero-day vulnerabilities become more readily available, the window for organizations to patch disclosed vulnerabilities is shrinking.
Phishing also continues to be a top tactic, as threat actors are constantly adapting their malware delivery methods to evade detection. According to a recent report by Egress, the finance sector is among the most targeted, alongside legal and health care. Business teams in finance, accounting, HR and marketing are the most frequently targeted. Threat actors are increasingly using HTML, PDF and Word attachments containing links to malicious sites and files hosted on trusted sharing platforms like Dropbox and Google Drive. The emerging use of artificial intelligence for more effective phishing campaigns is another concerning trend.
Credential theft and the use of compromised credentials remain effective tactics for infiltrating networks. Threat actors employ various methods — including stealer malware, password guessing, credential-harvesting pages and initial access brokers — to obtain valid credentials. Even multifactor authentication (MFA) is not foolproof, as threat actors have found success with bypass techniques like MFA fatigue attacks and the use of reverse proxy phishing kits.
Web compromise tactics, such as fake software update alerts and malvertising, trick users into installing malware by imitating legitimate brands or applications. Financial services organizations should be vigilant for fake websites that appear to be offering tools or software applications commonly used by their employees.
Supply chain attacks can lead to widespread impact in the financial sector. Scenarios include breaches of data hosted by third parties, compromises of managed service providers and breaches of software supply chains.
The risk of threat actors injecting malicious code into open-source software components is also a growing concern. In 2023, security company Checkmarx reported on malicious code packages uploaded to NPM, a JavaScript package hosting platform, specifically targeting the banking sector.

Geographic Hotspots and Threat Implications
North America
The United States is a prime target for ransomware attacks, as large financial institutions are particularly attractive to threat actors seeking big payouts. There are indications that some of this activity may be directed by Russian intelligence services with the aim of disrupting the U.S. financial sector.
South America
The South American region is known for the prevalence of dangerous banking trojans that target individuals and their financial information. Malware strains such as Casbaneiro, Guildma, Mekotio, Grandoreiro and the recent Chavecloak trojan are designed to infect users’ personal computers and mobile devices to facilitate banking fraud, with a particular focus on Brazilian users.
Ukraine & Europe
The financial services sector in Ukraine and Europe has been targeted by both nation-state actors and hacktivists in the context of the ongoing Russia-Ukraine conflict. Ukrainian intelligence services and pro-Ukrainian hackers have launched counterattacks against Russian financial institutions, and there is a risk that large-scale disruptive attacks, such as wiper malware, will be deployed by Russian APT groups against Western financial infrastructure. Pro-Russian threat actors have also conducted DDoS attacks against European and U.S. financial institutions, although these have generally had a low impact.
Middle East & Africa
In 2023, the financial sector in the Middle East and Africa region was one of the most targeted by threat actors. The region has seen a rise in impersonation scams, including attackers creating fake social media and messaging app accounts to impersonate executives and attempt to steal sensitive data or funds.
Asia & Australia
Some threat actors may perceive organizations in Australia and New Zealand as softer targets compared to their counterparts in Europe or North America, despite the significant steps taken by these countries to bolster the cybersecurity resilience of their critical sectors. Geopolitical tensions surrounding China’s aspirations over Taiwan have driven a significant amount of espionage activity against Taiwanese, Asian and U.S. organizations. While the financial services sector may not be the primary focus for Chinese threat actors, it still represents a critical industry that they likely seek to infiltrate.
Financial Services Vigilance Is Required
Despite the financial services sector’s more mature security measures, it will likely remain a top target for financially motivated and nation-state threat actors in the coming year.
While the role of artificial intelligence in bolstering threat actor capabilities is still being assessed, intelligence agencies and firms like Microsoft believe that while AI can help improve the efficiency and effectiveness of tactics like social engineering, code development and vulnerability research, it has not yet been observed to provide threat actors with novel, more dangerous or undetectable malware that cannot be countered.
Nevertheless, financial services organizations should continue to monitor advances in AI-enabled cyberattacks closely in case this situation changes.
To learn more and read the full text of QBE’s report, visit https://www.qbe.com/us/cyber.
This article was produced by the R&I Brand Studio, a unit of the advertising department of Risk & Insurance, in collaboration with QBE North America. The editorial staff of Risk & Insurance had no role in its preparation.










