Sponsored: Liberty Mutual Insurance
5 Tips to Get the Board Invested in Cyber Risk Management

Cyber attacks are growing in frequency, expense, and complexity. According to Security Magazine, more than 2,200 attacks occur each day, breaking down to one cyber-attack every 39 seconds. Whether these attacks result from human error or outright malfeasance, they cost companies dearly.
Ransomware attacks in particular have evolved into major financial threats. Gone are the days where hackers demand small sums to reduce their risk of getting caught. Now they ask for millions. And thanks to the interconnectedness of IT systems, an attack on one central vendor can bring down multiple entities at a time.
In early July, for example, a Swedish supermarket chain was forced to close more than 500 stores when a ransomware attack targeted not the chain itself, but its U.S.-based point-of-sale system provider. It’s estimated that roughly 200 businesses were affected by the breach.
“Cyber-attacks are getting larger. You have major corporations that have been completely stalled for weeks or even months due to a ransomware claim,” said Derrick Lewis, Senior Director, Cyber Risk Control, Liberty Mutual Insurance. “Because of that wide-ranging impact, cyber security is becoming less of an issue for the CIO, CISO or CTO and more of a board-level concern.”
Boards of directors need to understand their organizations’ cyber risk exposures and security posture and be prepared to take action when a breach happens. Board members who neglect to involve themselves in the cyber security program could potentially face stakeholder lawsuits in the event of an attack.
Here are five key strategies for increased board involvement in cyber security to help mitigate both cyber and directors and officers (D&O) exposure.
1) Align cyber security programs with business objectives.

Derrick Lewis, Senior Director, Cyber Risk Control, Liberty Mutual Insurance
Some cyber security programs focus on protecting high-value assets like customer data or on detecting a specific type of breach like malware. But with so many business processes reliant on technology (and technology vendors), cyber security programs need to become more comprehensive and holistic, aligning not just with discrete assets or exposures but with strategic business objectives.
“The key is to not just provide conventional, traditional cyber security capabilities, but to also understand what type of business you are, how you go to market, and what business processes are critical. How do you protect those processes that enable you to develop your product or service and deliver it to the market?” Lewis said.
“There isn’t a cookie cutter template for cyber security. Standards and frameworks exist as guidelines, but they should be customized and tailored to fit your business.”
That also means updating cyber security practices as a business evolves. As technology advances, businesses will adopt new tools and platforms and expand services accordingly. This creates new access points and vulnerabilities. Cyber security protocols should be reviewed and adjusted to that expanded attack surface.
2) Educate the board on the cyber risk landscape.

Vivian Freedman, Chief Claims Officer, IronPro Claims, Ironshore Insurance
Board members should receive regular briefings from the CISO or CIO regarding changes in the cyber risk environment, including external trends and emerging threats as well as internal changes in either exposure or risk mitigation strategies.
Ideally, these conversations should take place on a quarterly basis. Once-a-year dialogues aren’t enough to keep pace with the rapidly evolving landscape of cyber threats. Bringing in a third-party expert can also be beneficial to evaluate vulnerabilities and explain threats with objectivity.
“The CISO or CIO may want to defend their opinion, their outlook or their practices, which is only natural, but it can lead to the board getting a picture that’s rosier than reality. Bringing in an impartial, external expert ensures that senior leadership is getting all the facts, even if there are vulnerabilities,” said Vivian Freedman, Chief Claims Officer, IronPro Claims, Ironshore Insurance.
“Sometimes that’s necessary to ensure the board understands the full impact of cyber risk on their organization. They need that understanding in order to know what questions to ask and what risk mitigation initiatives to prioritize.”
3) Designate parties on the board that are accountable for cyber risk management.
The board can better hold a finger on the pulse of the cyber risk landscape if it has members directly responsible for cyber security oversight. Some corporations bring on a cyber expert just for this purpose, while others may appoint a cyber security subcommittee. This team of stakeholders that holds functions across the organization can provide insight to the board on the health of the company’s cyber risk program.
“I have met with C-suite leaders who are daunted by the frequency of cyber security dialogues we recommend they have with the board. They worry about overwhelming board members who already have a lot on their plates. Having a designated individual or committee to handle the cyber security program helps to alleviate that,” Lewis said.
A cyber security subcommittee could be part of an existing risk management committee or it could exist as its own entity. To be effective, it is important that the subcommittee is aligned with the board-level committee and has a formal process for reporting to the board.
In any case, “it’s incumbent upon the board to have someone with cyber security expertise among their ranks to ensure this risk stays on their radar,” Lewis said.
4) Create a clear understanding of third-party risk management.
The larger a company’s vendor network, the larger their exposure to breaches or attacks. Any time an organization initiates a new relationship in which technology systems will be linked, due diligence must include evaluating that vendor’s cyber security practices and level of cyber insurance. Organizations that don’t dig into these details could be left on the hook in the event of a vendor system breach.
“We saw one instance in which a vendor that operated the insured’s payment system was breached. The vendor had very low limits of cyber insurance coverage, while the insured had a large insurance tower. So even though a weakness of their vendor was to blame, the insured will still have to respond to that breach. They will end up paying tens of millions and won’t even be able to recover against their vendor, because the vendor’s limits will be exhausted,” Freedman said.
“It’s critical before a cyber event occurs to understand a vendor’s defenses, and their insurance coverage. Because their exposure is your exposure.”
Of course, it’s not realistic to have the board involved in every vendor relationship, but we recommend that boards understand the overall approach to third-party risk management, including the metrics by which partners are evaluated and which vendors are most critical to the organization’s operation.
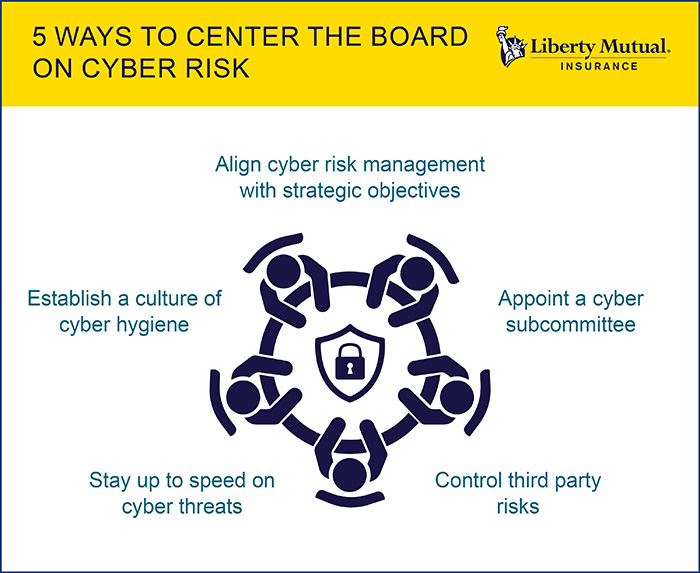
5) Create a top-down culture of cyber security and transparency.
When the board demonstrates a commitment to cyber risk management, it sets a tone that permeates throughout the organization. Every level of a company becomes more aware and more vigilant when senior leaders establish cyber hygiene as a priority.
“Right now, cyber risk management is very reactive in most organizations, but to have the board engaged in the cyber dialogue shows that importance at the highest levels of the organization. Board involvement tends to apply a little bit of pressure on the CISO and the cyber team to ensure that they’re operating effectively, keeping up-to-date on the latest trends, and providing the right information in a timely manner,” Lewis said.
Transparency should, however, accompany this pressure so employees feel empowered to speak up about any vulnerabilities they identify.
“There’s a real risk that people will want to downplay when they see risks, because they don’t want to be the one to cause concern. It’s important to change that mindset, and the board can influence culture. Breaches can be prevented when employees at every level feel they can be vocal about security weaknesses,” Freedman said.
Leverage Carrier Experience and Expertise
When it comes to managing cyber risk, working with an insurer with specialized expertise is critical. A carrier with the right resources helps organizations get proactive about identifying and mitigating cyber exposures and can help risk managers engage the board with confidence.
Liberty Mutual’s cyber underwriters and claims professionals work with brokers and partners on a consolatory basis to build strong cyber insurance solutions.
“Our claims team is always happy to talk to a new insured. We walk them through the claims process proactively, so they know what steps to take first and which vendors to engage. In many cases, this conversation helps to refine their response plan, and it helps the process go more smoothly if a claim eventually does occur,” Freedman said.
Insureds can also report incidents through a 24/7 hotline or app that connects them directly to the cyber claims team.
“We aim to respond as quickly as possible to those alerts. We work to get them connected to the right parties and have security experts look into their system to help mitigate the damage. We strive to provide the greatest value to our insureds experiencing a cyber event,” Freedman said.
By having input and buy-in from the board to be proactive about cyber risk management, a company can better protect itself against cyber threats and related stakeholder lawsuits and D&O claims.
To learn more, visit https://business.libertymutual.com/commercial-solutions/professional-liability/cyber-liability/.
![]()
This article was produced by the R&I Brand Studio, a unit of the advertising department of Risk & Insurance, in collaboration with Liberty Mutual Insurance. The editorial staff of Risk & Insurance had no role in its preparation.








