Business Interruption Risk
Severed Communications
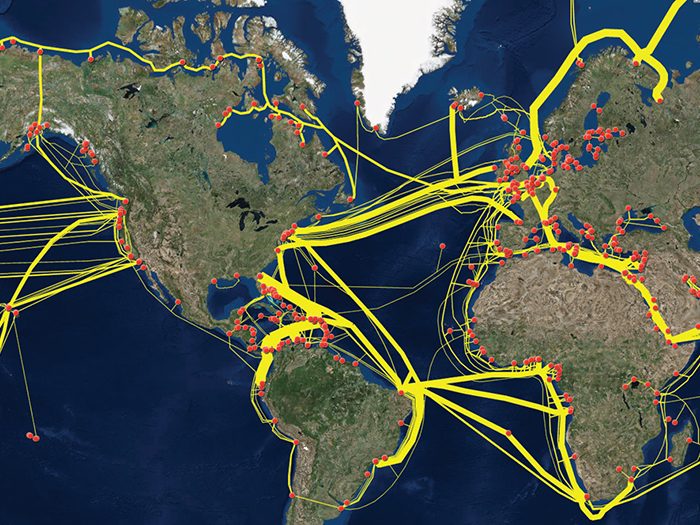
Crisscrossing the ocean floor, undersea optical fiber data cables are an essential component of an increasingly interconnected world, quietly carrying massive amounts of data communications between the Earth’s landmasses.
But they are not invulnerable. Individual cables are severed or damaged dozens of times each year, most commonly by fishing boat anchors, but also by storms, scrap collectors and even shark bites.
The U.S. and other major markets, like Europe and Japan, are served by numerous cables, providing enough redundancy that traffic from a single damaged cable is rerouted before end users even notice. Wider outages, however, can have more far-reaching effects.
VIDEO: IDG.TV follows along as undersea data cables are manufactured and then loaded aboard a ship to place them in the ocean.
That’s why in October 2015, when Russian ships were observed lurking near undersea data cables, U.S. military and intelligence officials were concerned about possible sabotage.
Some experts, however, see that as unlikely.
“Cables during peacetime are protected by law under the provisions of the United Nations Convention on the Law of the Sea,” said Keith Schofield, general manager of the International Cable Protection Committee, representing the submarine cable community of interest.
Attempted sabotage, he said, would likely be detectable and stopped before any significant harm could be done to trunk cable routes.
“Before 10 or 20 percent of them were affected, owners would realize that something pretty serious was happening and could respond appropriately.”

Sean Donahue, assistant vice president and underwriter, XL Catlin
Sean Donahue, an assistant vice president and underwriter specializing in cyber and technology at XL Catlin, agreed.
“These commercial cables have too much intrinsic value,” Donahue said. “Anybody who may have that sort of capability, such as Russia … would be hurting their own self-interest.”
Seismic activity, however, has been known to damage enough cables to cause wide service interruptions and service degradation, even in areas with ample cable connections.
A 2006 earthquake in Taiwan severed several undersea cables, causing major disruptions in Asia and ripple effects that interrupted phone service to Europe. Smaller incidents can have far reaching impacts, as well.
In 2013, a string of separate cable cuts in Egypt caused widespread data slowdowns in large portions of Africa and Asia.
And a single cut off of Northern Ireland in 2015 sparked headlines claiming it had “sent broadband into meltdown.”
When cables are cut, rerouted data can overwhelm unaffected networks, causing slowdowns even for those not directly affected. Smaller countries with less redundancy — and the companies doing business with them — can suffer substantial repercussions from such events.
Even in the U.S., outages involving multiple cables could cause data traffic to be rerouted to undersea cables on the opposite side of the country, potentially triggering domestic slowdowns along the way.
As businesses become increasingly dependent on fast data communications, even minor slowdowns can impede business. For web-centric and cloud-based companies, as well as content providers, such slowdowns could be a serious problem.
According to TeleGeography, a data cable industry research firm, Google and Bing report that minor lags lead to decreased click-throughs and search result views, and “Amazon has claimed that every 100 milliseconds of latency reduces its sales by 1 percent.”
High-frequency trading companies sometimes own dedicated data cables, but others are dependent on the same networks as the rest of us, and if those networks slow down, it hampers performance and costs them money.
Built with Redundancy
The undersea cable industry goes to great lengths to ensure uninterrupted service.

Peter Jamieson, chair, European Subsea Cable Association
“The systems are built with redundancy in mind,” said Peter Jamieson, chair of the industry group European Subsea Cable Association.
“You should always aim to have at least two cables from each operator so that if you lose one cable … you automatically switch onto the other one. The redundancy is built into the network on the global network as well.”
Excess capacity is also built into the system. Most cables were originally built to handle optical data traffic in a single wavelength, but they now use a technique called Dense Wave Division Multiplexing (DWDM), which handles many wavelengths.
“We are now getting potentially 400 times the capacity on one optical fiber than what you probably got 15 to 20 years ago,” Jamieson said.
Routing protocols ensure that in the case of a service interruption, data instantaneously finds alternate routes. And the different cable owners work together in various consortia to operate roughly 60 cable-repair ships throughout the world, which are on call to ensure that any damage is repaired quickly. Repairs generally take a minimum of four days to complete.

But according to Helen Thompson, director of commercial marketing at Esri, a software company specializing in geographic information systems, it is not inconceivable that the individual smart systems meant to ensure seamless rerouting could have unexpected results — much the way automated trading programs can produce dramatic and unexplained lows or highs in financial markets.
“Those individual response plans come together and aggregate in such a way that they themselves might have an impact,” Thompson said.
“It’s like the butterfly effect. … That’s increasingly the nature of connectivity and a consequence of the very widespread, multi-point-of-touch communications network that we rely on.”
While DWDM vastly increased capacity on data cables, demand and usage have been steadily catching up as businesses and individuals demand and depend on more and more data.
A company called Hibernia Express recently laid a pair of superfast transatlantic cables, the first new cables in 13 years. More may be on the way.
“The content people want to have their own fibers right now,” said Jamieson.
“Can you prove that you would have made X amount of dollars versus Y amount of dollars because of a degraded service?” — Sean Donahue, assistant vice president and underwriter, at XL Catlin
“So the Facebooks, Googles, Amazons and Microsofts of this world … they want to have their own fiber to control their own traffic on cable, so they are driving a lot of new systems as well.”
It is a sign of how seriously data-driven businesses take their dependence on fast, dependable transmission infrastructure.
As data usage skyrockets, Thompson cautioned against taking network resiliency and capacity for granted.
“We could be in a situation where ‘out of sight, out of mind’ [and] all these things are running at 99 percent capacity, and we’re one point … away from total failure.
“We don’t know. I’m not suggesting that is the case, but it behooves us to provide evidence that we have redundancy and resilience in the systems that we’ve become reliant on. We increasingly are engineering our future to be more dependent on them.”
Smart houses, self-driving cars, and other web-dependent gadgets and systems will not only add to data traffic, but to the list of systems that could malfunction in the case of outages and slowdowns, opening new areas of risk for homeowners, as well.
Protecting Data Flows
Traditional business interruption coverage focuses on perils like flood and fire, power outages and physical infrastructure failures.

Helen Thompson, director of commercial marketing, Esri
“But, when we move to businesses where data is a utility, we have a different sort of business interruption, and that is going to be increasingly important to service-based economies,” said Thompson.
“We think about site liability and data breaches, but what I think we’re going to start moving to more and more is providing business interruption insurance around data.”
Cloud coverage insurance is still a rarity, but probably not for long. “Many more companies should think about cloud computing insurance,” she said.
“It will become a vital part of what’s included in business interruption insurance.”
Businesses should know their providers’ contractual obligations and dependent business interruption coverage in case of outages, as spelled out in the service level agreement, she said.
“More and more major businesses are expecting that as part of their service level agreement,” Thompson said.
“I think that will become an integral part of the transfer of risk and liability. If you’re completely dependent upon the web and the cloud to do business, and you don’t protect yourself with a service agreement on the cloud provider, you’re going to be subject to claims from other people. So, that discussion with your insurance provider should be absolutely central.”
Even with coverage, however, calculating business interruption losses, especially for traders and other market-dependent businesses, can be extremely difficult, particularly during incidents that may themselves be roiling the markets.
“Can you prove that you would have made X amount of dollars versus Y amount of dollars because of a degraded service?” Donahue asked. “There’s a lot of moving parts to that scenario.” &










