Cyber Coverage
Navigating the Minefield

Over the past two decades, traditional lines, from GL to crime to property, have increasingly included some form of cyber cover as standard, while cyber underwriters have done their best to sculpt stand-alone policies that react to the evolving nature of both the risk and client demands. But for those seeking to buy their first stand-alone cyber policies, the landscape can be daunting.
Cyber specialist Lynda Bennett, chair of the insurance practice for law firm Lowenstein Sandler, described the increasingly crowded stand-alone cyber market as a “minefield” in which terminology, exclusions, terms and conditions can “vary wildly” from form to form.
“We are asked to review cyber policies because they can be unbelievably complex. While the appetite and demand is there for coverage, the nature of the risk is in flux and insurers are having as much trouble pinning down what risk they are willing to insure as risk managers are trying to work out what risks they need insurance for,” she said.
“Each year the traditional industry tweaks its exclusions to push buyers into a dedicated cyber policy. Then they are left in the Wild West having to negotiate a new policy,” said Bennett.
Marsh’s cyber product leader Bob Parisi believes that consistency of approach is appearing in tranches of the industry — such as underwriters who wish to write primary versus those who write excess, those who favor large companies over SMEs, and those who focus on privacy/liability versus those who underwrite direct first-party losses.
According to Jason Glasgow, vice president and practice lead for technology, privacy and network security professional liability with Allied World U.S., it is mainly terminology, not coverage, which sets most of today’s cyber policies apart. But there is no doubt first-time buyers can easily find themselves inadequately covered if they’re not careful.
Mind the Gap
Once predominantly serving to protect customer-facing sectors against data privacy breaches, the scope of cyber cover has expanded into many new areas including property damage, business interruption (BI) and bodily harm. Cobbling together adequate cyber coverage between traditional property, GL and crime policies is increasingly challenging.
However, buying stand-alone cyber cover is not a magic bullet; sources all agree that gaps in coverage may still remain — particularly as far as property and BI are concerned.
Many underwriters are cautious, treating every applicant as “the virtual equivalent of a stilt house on the Gulf Coast.” — Bob Parisi, managing director, Marsh FINPRO
“BI cover in the cyber space is growing but is still limited,” said Parisi. “A risk manager who knows what their property policy would pay out on a loss due to fire would find the BI cover in a cyber policy looks like property language but doesn’t truly mirror the way a property policy deals with a loss.
“Cyber focuses mainly on the IT side, nonphysical perils, and is missing around two-thirds of what a traditional property policy would cover for physical peril,” he said.
“The challenge facing cyber underwriters is how to bridge the gap between where traditional P&C forms leave off and the current cyber wordings begin. Clients don’t care what ‘silo’ the insurance market decides to place the risk in, just that it is covered.”

Bob Parisi, managing director, Marsh FINPRO
A lack of loss history, fears over risk aggregation and uncertainty over how companies will react to cyber-triggered BI events mean many underwriters are cautious, treating every applicant as “the virtual equivalent of a stilt house on the Gulf Coast,” Parisi added.
Waiting periods are one area of concern in cyber BI policies. According to Kevin Harding, partner at RGL Forensics, typical cyber insurance policies include a waiting period of four to 12 hours before BI cover begins to apply. Depending on the nature of the cyber event or the business, this means anything from none to most of the sales loss could fall within the waiting period and therefore not be covered.
“To avoid this situation, and give more certainty to both the insurer and policyholder, we feel either a fixed monetary deductible or possibly a franchise deductible could be adopted,” he said.
“Once the losses are in excess of the defined monetary amount, both parties know what will be paid and no hourly calculation is required.”
However, Harding noted, insurers would need a lot more information about the value of the potential exposures at the time of underwriting the policy to determine the deductible values.
Terrorism is another “area of discomfort” for policyholders and insurers, with Bennett arguing that the definition of what constitutes a terrorism trigger is even vaguer under a cyber policy than other policy forms. “Several recent losses are speculated to be politically motivated, but many cyber policies exclude terrorism whether it is declared or undeclared as a terrorist act, leaving insureds on uncertain ground and heading towards coverage disputes with their insurers.”
Collaborative Approach
Buying stand-alone cyber property or BI cover needs to be carefully woven into a company’s overall program. Certain serious property damage coverages may be best off under a property policy that is likely to have greater limits and a different pricing scheme than a cyber policy, Glasgow said.
“Clients may not want their cyber policy to erode limits in their crime, E&O, D&O or property policies — they have those limits in place for a reason and need to maintain separate limits to ensure proper coverage,” he said.
Further, when two or more policies provide overlapping first-party property coverage it can create an uncertain outcome if a loss occurs, as each insurance policy will likely contain ‘other Insurance’ provisions that make each of them excess to the other.
“Each year the traditional industry tweaks its exclusions to push buyers into a dedicated cyber policy. Then they are left in the Wild West having to negotiate a new policy.” — Lynda Bennett, insurance practice chair, Lowenstein Sandler
“This has the potential to lead to uncertainty at the worst possible time — after the loss has happened,” said Grace Ries, head of cyber risk insurance products at FM Global, whose new product, “Cyber Optimal Recovery,” allows clients to position their property policies to maximize recovery alongside cyber or designate property as primary in order to preserve the cyber policy’s non-property limit.
 Steve Anderson, cyber liability product executive at QBE, said some of the next steps in cyber product development are likely to include micro insurance, artificial intelligence and Internet of Things liability coverages, as well as cyber “all risk” policies — though only if the industry can come to grips with potential risk aggregation.
Steve Anderson, cyber liability product executive at QBE, said some of the next steps in cyber product development are likely to include micro insurance, artificial intelligence and Internet of Things liability coverages, as well as cyber “all risk” policies — though only if the industry can come to grips with potential risk aggregation.
Beazley has taken a step in that direction, partnering with Munich Re to offer what it terms “holistic” cyber cover — catastrophic limits (up to $100 million at present) and broad coverage against virtually any type of cyber loss.
This type of cover can be bought either as primary to any other type of cover, or to dovetail around existing policies — the latter approach requiring a collaborative approach. According to Paul Bantick, Beazley’s leader for technology, media and business, the specialty insurer is seeing huge demand for the product and is already working with about 50 large corporate clients to design holistic programs.
But, noted Jill Salmon, head of cyber/tech/MPL at Berkshire Hathaway Specialty Insurance: “If we are going to start writing holistic programs, broadening cover to include social engineering, crime coverages and property damage, or expanding cover to nonsecurity breach triggers such as system failure, this is not necessarily what cyber underwriters have grown up understanding, so broadening expertise in cyber is critical, as is working collaboratively with experts in other lines of insurance.”
For this reason, Salmon and others believe cyber still has a future within traditional lines such as property and crime, as well as other lines of coverage. “Cyber is a cross-line coverage. As other lines recognize cyber events as a cause of loss, they will have to integrate the cyber discipline,” she said.
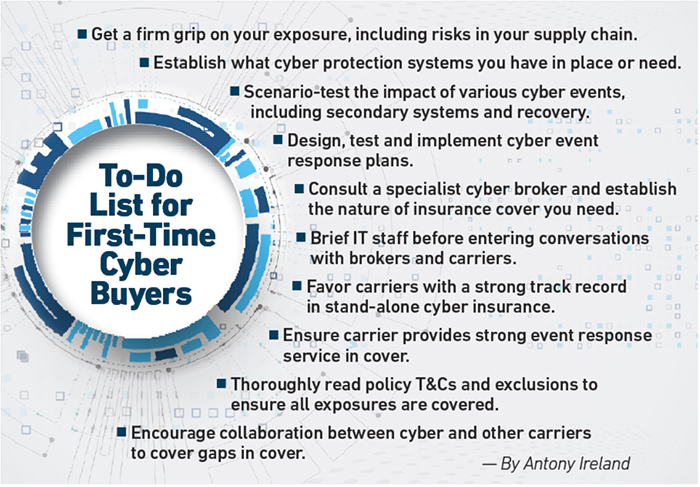
With cyber products and inclusions only set to proliferate further, employing a specialist cyber broker is essential.
A good broker will not only help the client better understand what the most appropriate coverages are for their exposures, but can also negotiate better terms from carriers and in the case of bigger players may have already negotiated a degree of cross-carrier standardization of wordings through its work with other clients.
Holistic coverages may go some way toward simplifying the process for large firms, but for the majority, the future may hold an even wider choice of options as cyber grows both stand-alone and as a component of a wider array of covers.
Getting expert advice is an essential tool to help navigate the market. &











