An Inevitable Threat
Cyber: The New CAT
Superstorm Sandy. The Joplin tornado. The Japanese earthquake and tsunami. California wildfires. 9/11. Catastrophes come in many forms. It is universally understood that despite our best efforts, disaster can strike due to forces beyond our control. Cyber threats are equally dangerous and diverse — and just as unstoppable.
Yet even as catastrophe risk management matures and scores of executives join the catastrophe conversation, the dragon known as cyber risk still sits in the middle of the board room, quietly smoldering.
In every industry and at every company size, cyber risk is a foundation-level exposure that every business must confront — one that must be viewed with the same gravity as a company’s property, liability or workers’ comp risks.
As recent as a decade ago, that might have been an overstatement. But not now. Technology and business are fundamentally linked. Computers and the Internet are the primary platform for communicating with customers and vendors, managing profits and expenses, paying employees, operating the machines that produce goods and provide services, and making sure that the end product gets into customers’ hands on schedule. Mobile technology and the Internet of Things are opening new channels, making technology a physical extension of ourselves, both personally and commercially.
“The entire economy is so reliant, in ways that we don’t even see, on technology and the storage, transmission and usage of data, both personal and for analytical purposes, that it’s fundamental to almost every sector,” said Oliver Brew, vice president for professional, privacy, and technology liability at LIU Liberty International Underwriters, the specialty line division of Liberty Mutual in New York.
Video: Computer security expert Mikko Hyppönen explains how he tracked down the creators of the first PC virus, which hit the net 25 years ago, and how to stop the new viruses of today.
That reliance is only going to grow. A January report by Forrester Research described software assets as more critical to business success than financial assets over the next 20 years.
“If you take a look at the public companies’ 10-Ks and publicly disclosed statements, what are they emphasizing that’s going to differentiate them from their competitors, increase sales, decrease costs and maximize efficiency? They focus on the use of technology and the use of information assets,” said Kevin Kalinich, global practice leader for cyber and network risk at Aon Risk Solutions.
With increased technology comes increased opportunity for attack. However, that reality didn’t get a lot of traction in the C-suite until the recent Target breach splashed it across world headlines. Even now, there are still some resting easy, confident that their IT teams have everything under control. Others assume cyber attacks are a threat largely confined to industries such as retail, health care and financial services — sectors with the most data to lose.
Small businesses, in particular, downplay the risk, said Jesse Bessler, an account executive at Lacher & Associates, of Souderton, Pa. “I think it’s that they just don’t understand the risk, and they think that [a cyber policy] is an add-on item they don’t need.”
Increased Sophistication
Security experts, however, are trying to break through the wall of denial. Cyber attacks, they argue, are akin to massive storms or similar to the focused destruction of a tornado — something you can prepare for, but not something you can prevent. Despite firewalls and antivirus programs, experts say, cyber punches will eventually land inside every company.
To grasp the magnitude of the threat, it’s important to recognize that the driving forces behind cyber crime are vast, varied and as uncontrollable as any atmospheric or geologic force. The threat is now ubiquitous, and experts agree that while making an effort to reduce the risk of a breach is important, it is no longer possible to completely prevent cyber attacks.
“It’s like two identical cars in a mall parking lot,” explained Kurtis Suhs, vice president and national technology and privacy product manager for Ironshore. “If one’s locked and one’s unlocked, the bad guy’s going to go to the unlocked car. But if the bad guy really wants to get into the locked car, he will — it’ll just take longer.”
And yet, organizations keep brushing off the threat. That may be because “cyber risk” has become synonymous with data theft. If an entity does not have a significant aggregation of customer financial data, executives assume they won’t be targeted. The reality is that the true exposure is no longer just about credit card or Social Security data. Hackers have expanded their target list, adopted a more patient approach and found deep-pocketed sponsors, whether private-sector or state-sponsored, security experts said.
Sophisticated hackers are conducting long-term surveillance and probing for weaknesses they can exploit for financial gain, said David Remnitz, global and Americas leader of Ernst & Young’s forensic technology and discovery services business. “The end result here is the theft of highly valuable, internal information for significant financial gain,” he said.
While that could mean outright theft of trade secrets or confidential M&A data, it could also mean corporate sabotage, as in corrupting a decade of research and development results or putting competitors out of business. Imagine a market where most of the players used one primary vendor as a source for a key ingredient. An organization could contract with a lesser-used source for that ingredient, then disrupt the operations of the primary vendor via a denial-of-service attack or other type of malware, leaving the rest of the market scrambling for suppliers.
The potential for lost business and liability claims could be devastating for the affected companies. Even those with solid business continuity plans in place could still take heavy hits from the reputational fallout.
“A large company might be able to absorb that risk. A small company can’t,” said Elissa Doroff, a vice president and senior advisory specialist in Marsh’s network security and privacy practice in New York.
To date, breaches have largely been limited to individual companies, but the potential for larger events looms. One concern centers on cloud companies, which could host data for hundreds of businesses. A data breach or network interruption, or the physical destruction of a cloud-service data center could wreak larger havoc on the economy.
“That’s a potentially catastrophic loss,” said Doroff.
The sky’s the limit at this point. Criminals are capable of disrupting a multinational corporation, a transportation or logistics network, a health care system, an entire industry or even an entire region, creating havoc and leading to economic losses in the millions or billions — in many situations even putting lives at risk.
Keep in mind that those with ill intent don’t even need to have an IT background — the proliferation of hackers-for-hire means that anyone intent on doing damage can do so if their pockets are deep enough.
That said, it probably wouldn’t take a well-funded ring of genius-level hackers and a sophisticated attack plan to paralyze the average organization. Three years ago, the U.S. subsidiary of Shionogi, a Japanese pharmaceutical firm, suffered a devastating cyber attack that deleted the contents of 88 computer servers, crippling the company’s operations for several days, disabling its email, BlackBerry servers, order-tracking system, and financial management software. The attacker? A former mid-level employee, working from a public
Wi-Fi network at a nearby McDonalds, calmly sipping coffee while bringing Shionogi to its knees.
An Enterprise Approach
Even organizations that have never been affected by a catastrophe generally do not question the need for CAT planning. At the very least, most probably have a written evacuation plan in place and enough insurance to cover the potential physical damage of a storm. The smartest also address the whole picture from a supply chain and business continuity standpoint, and may have even considered questions about how to manage any reputational damage related to interruption of service to customers.
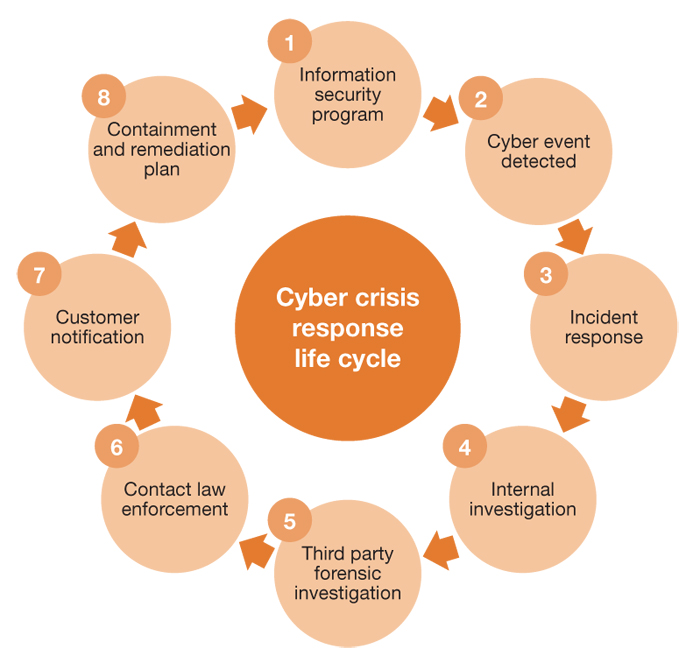
PwC’s report, Cyber Crisis Management: A Bold Approach to a Bold and Shadowy Nemesis, offers a new philosophy and approach to incidence response. This graphic shows the key elements of a structured cyber crisis response.
Cyber exposure should be approached in much the same way. It starts with engineering out the risk to whatever extent possible. If your roof is old, for instance, replacing it may be a way to ensure the building is more likely to stay intact if it’s battered by a storm. The cyber equivalent might be replacing old servers or upgrading any existing automated intrusion detection system. Security experts stress, however, that cyber risk is not an IT exposure, it’s an enterprisewide exposure. Therefore vulnerabilities need to be identified across an entire organization, with policies and procedures modified accordingly.
A comprehensive, enterprisewide disaster plan can also go a long way toward helping companies minimize the damage sustained in the event of a cyber attack. For every function of an organization, management needs to ask hard questions about how a cyber attack could disrupt that function, and what kind of back-up plan each department would need. Do you have a way to contact customers and suppliers if your email goes down? Do you have a crisis communication plan for alerting the public about how you’re handling the situation? Are your records backed up and accessible through a secure third-party?
Increasingly, organizations will rely on insurance to ensure their survival after a cyber event. In a February survey by BAE Systems, nearly 30 percent of companies said they expected the cost of a cyber attack to exceed $75 million. Another 20 percent expected the cost to fall between $15 million and $75 million.
“There’s an expectation that this could have an extremely material effect on business performance, and that’s a risk they look to hedge,” said Paul Henninger, global product director for BAE Systems Applied Intelligence, a business unit of BAE Systems.
Taking a realistic approach to cyber attacks could improve underwriting of the risk, he said. Just as carriers evaluate whether clients are prepared for a CAT-5 hurricane, knowing some damage is likely, they could determine whether clients are ready for a cyber storm.
“You can’t make it go away, but you can minimize the impact on the bottom line and customers and reputation,” he said.
Complete coverage on the inevitable cyber threat:
Risk managers are waking up to the reality that the cyber risk landscape has changed. Every sector must prepare to withstand the storm.
 Critical Condition. The proliferation of medical devices creates a host of scary risks for the beleaguered health care industry.
Critical Condition. The proliferation of medical devices creates a host of scary risks for the beleaguered health care industry.
 Disabled Autos. It’s alarmingly easy for a hacker to take control of a driverless vehicle, tampering with braking systems or scrambling the GPS.
Disabled Autos. It’s alarmingly easy for a hacker to take control of a driverless vehicle, tampering with braking systems or scrambling the GPS.
 Unmanned Risk. The dark side of remote-controlled drones, which have already been hacked — by students.
Unmanned Risk. The dark side of remote-controlled drones, which have already been hacked — by students.
 An Electrifying Threat. There is a very real possibility hackers could devastate the nation’s power grids — for a potentially extended period of time.
An Electrifying Threat. There is a very real possibility hackers could devastate the nation’s power grids — for a potentially extended period of time.
Related articles:
Heading Off ‘Cybergeddon’. Experts say resistance is futile, but resilience is paramount.











