2015 Most Dangerous Emerging Risks
Corporate Privacy: Nowhere to Hide

SCENARIO: In a small apartment in Atlanta, Pete scanned the hardware in front of him. His fingers flew as he deftly navigated multiple windows. A former defense contractor employee, Pete possessed a highly specialized set of skills.
He knew how to hack into almost anything, from network servers and credit card databases, to VoIP phone systems and video conferencing systems. An encryption expert, he knew how to exploit every weakness and sniff out every back door. Pete never met a digital lock he couldn’t pick.
Pete’s talents — and his reputation for discretion — kept him in demand, especially in certain circles.
His latest gig was gathering intel on Odyssey International for one of Odysseys’ top competitors, especially an inside track on any mergers or acquisitions Odyssey might have up its sleeve.
Pete pulled up his files for several key Odyssey execs and smiled smugly. People like Garry Buchanan made Pete’s job way too easy.
An encryption expert, he knew how to exploit every weakness and sniff out every back door. Pete never met a digital lock he couldn’t pick.
Odyssey’s U.S. head of new business development, Buchanan was tech-obsessed. From the moment Buchanan hopped into his Tesla Model S and engaged the autopilot until he arrived at work, Pete could peek at every email, calendar entry and company report. Buchanan’s smartphone let Pete keep track of him out of the car too, whether he was picking up a latte or checking in for a flight.
Accessing Odyssey’s network was a little tougher than Pete expected — its security was more sophisticated than most. But, like most companies, it spent more time protecting its customer and finance data. Its email server was far less secure. Its phone system was barely protected at all.
Around 8:15 a.m., Pete’s system alert let him know that Buchanan was on the phone. It sounded like Odyssey was researching a potential acquisition.
Pete tapped the screen to record the call and sent an encrypted file to the man who’d hired him.
Buchanan’s flight to London arrived on time. He’d checked into his hotel and stayed there all night. But Pete was drumming his fingers on his desk, aggravated. There were meetings on Buchanan’s calendar. But with whom? There was no data.
There had been a few vague email references, but nothing that had given Pete a clear picture of what was up. Buchanan seemed to be deliberately keeping the details under wraps.
“We’ll see about that,” said Pete, firing up more hardware. He checked the time and calculated the time difference. Buchanan would probably be leaving the hotel soon.
He’d found Buchanan’s Uber account the day before and guessed he’d be using the service. Sure enough, he’d already been picked up. “Gotcha,” said Pete, gaining unauthorized access to Uber’s “God View” and tracking the car’s route.
Ten minutes later, Buchanan walked into a café and was seated at a table out front. Pete watched in real time as Buchanan took a moment to take in the London scenery while waiting for his breakfast companions.
“Bless those Brits,” thought Pete. “And their millions upon millions of CCTVs.”
Buchanan’s two guests arrived a few minutes later. Pete was pleased to have a good angle on both of them. He locked on their faces and dragged the images into his facial recognition program. He got a match on both and searched their records. One was a visiting fellow at the University of Cambridge in the department of engineering. Interesting.
Pete kept digging. An hour later, Pete had enough data on both of them to get a picture of what Buchanan was up to and why Odyssey wanted this little excursion to be kept under wraps.
Time for another file upload to his new corporate benefactor. This info was hot.
“I should’ve charged him twice as much,” Pete thought ruefully as he sent his customer the information on his competitor’s latest move.
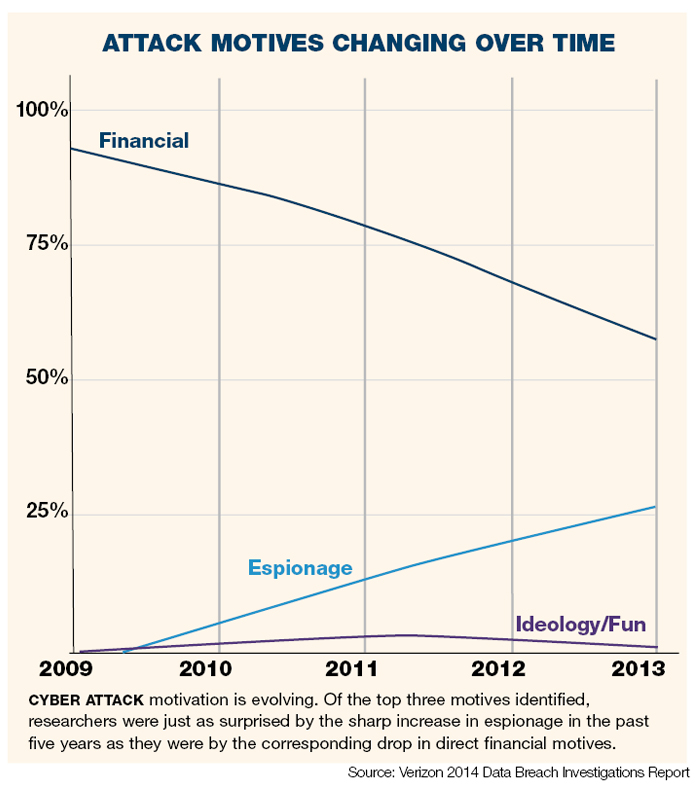
ANALYSIS: There are no more secrets. The lesson brought home by WikiLeaks and later by Edward Snowden is that privacy is a quaint notion of a bygone era. We are in, as it has been dubbed, the “Golden Age of Spying.”
Everyone now knows that the U.S. National Security Agency (NSA) has access — on a massive scale — to chat logs, stored data, voice traffic, file transfers, phone records, email and social networking data. It can also access web chats, Internet searches, text messages … the list goes on.
The agency has long had a certain amount of cooperation from major technology companies including Microsoft, Yahoo, Google, Facebook and Apple. Unbeknownst to some, it also engineered a weakness in an encryption standard, allowing back-door access to those companies, and their data.
Problem is, if you leave the back door open, you can’t guarantee that others won’t find their way in.
Now factor in the Internet of Things. Estimates suggest there could be up to 80 billion connected devices in use five years from now — devices that can monitor anything from the climate quality in your delivery trucks to whether the plant in your window needs more sun.
From your digital world to your physical world, everything will be hackable, trackable, visible. Everything will have the potential to be seen by someone you never intended to share it with.
That’s happy news for those set on malfeasance, either to steal corporate secrets or engage in disruption for fun or profit. But it’s troubling for businesses of all sizes as they face the challenge of protecting what they can and managing the rest.
“What you’re going to see is a more formalized way of communicating sensitive information and housing sensitive information,” said Randy Nornes, executive vice president with Aon Risk Solutions.
“So if you have key data that creates value for your firm, I think you’re going to see that the fundamental technology architecture that people use to store the really important stuff will be remote and distant, and it won’t be readily accessible through the Internet.”
But it’s the day-to-day actions of conducting business that organizations will have more trouble keeping behind locked doors.
“In a fully transparent world … companies will have to behave as if every action will be reported on the front page of their local paper,” said Nornes’ colleague Paul Kim, co-CBO of Aon Risk Solutions U.S. Retail operations.
Futurist and author David Brin said in a recent interview with “Variety,” that organizations can’t “count on anything staying secret for more than 10 years, that’s delusional on the border of psychosis.
“Get used to the notion that some day, someone is going to hear this conversation or read this document. And live and work as if anybody might be watching now,” Brin added.
Along with those inevitable leaks come serious risks to brand and reputation, which is why reputation risk management will need to develop at least as fast as privacy erodes.
That means using an extremely thorough process of scenario planning, and understanding exactly how any kind of breach, leak or competitive attack could affect the company’s value and its ability to conduct business.
“It’s not something that’s limited to the public relations team; it’s not something that’s limited to a chief communications officer,” said Chris Lukach, president of Anne Klein Communications Group, LLC.
“It’s something that needs to be shared among risk management, legal, HR, operations … . That to me is what makes companies prepared.”
There are multiple points at which hyper-transparency can result in a business loss, and insurance products will no doubt keep evolving to meet those needs. In a case where a release of confidential information might damage a company’s image, for instance, Tokio Marine Kiln is already underwriting a product that goes beyond traditional cyber insurance and helps companies insure against that spectrum of losses.
Explained Tom Hoad, underwriter at Tokio Marine Kiln, a Lloyd’s syndicate, risk managers have become increasingly sophisticated in the way they think about their exposures.
“[They’re asking], ‘Where are the key performance indicators for the company and what sorts of things can affect our ability to deliver on those things?’ … The preservation of brand equity, is very much at the forefront of that process.”
Complete coverage of 2015’s Most Dangerous Emerging Risks:
 Corporate Privacy: Nowhere to Hide. Rapid advances in technology are ushering in an era of hyper-transparency.
Corporate Privacy: Nowhere to Hide. Rapid advances in technology are ushering in an era of hyper-transparency.
 Implantable Devices: Medical Devices Open to Cyber Threats. The threat of hacking implantable defibrillators and other devices is growing.
Implantable Devices: Medical Devices Open to Cyber Threats. The threat of hacking implantable defibrillators and other devices is growing.
 Athletic Head Injuries: An Increasing Liability. Liability for brain injury and disease isn’t limited to professional sports organizations.
Athletic Head Injuries: An Increasing Liability. Liability for brain injury and disease isn’t limited to professional sports organizations.
 Vaping: Smoking Gun. As e-cigarette usage rises, danger lies in the lack of regulations and unknown long-term health effects.
Vaping: Smoking Gun. As e-cigarette usage rises, danger lies in the lack of regulations and unknown long-term health effects.
Aquifer: Nothing in the Bank. Once we deplete our aquifers, there is nothing helping us get through extended droughts.
Most Dangerous Emerging Risks: A Look Back. Each year since 2011, we identified and reported on the Most Dangerous Emerging Risks. Here’s how we did on some of them.